Securing Your DevOps Pipeline - Implementing NuGet Vulnerability Checks
— Code, Azure, Security — 3 min read
In today's software development landscape, security is paramount. With cyber threats evolving constantly, it's crucial for developers and DevOps teams to stay vigilant against potential vulnerabilities in their code dependencies. One such area of concern is NuGet packages, commonly used in .NET projects. In this blog post, we'll explore why checking for NuGet vulnerabilities is important and how you can integrate this crucial step into your DevOps pipeline.
Why Check for Vulnerabilities?
Before delving into the specifics of NuGet vulnerability checks, let's first understand what a vulnerability is. In the realm of software, a vulnerability refers to a weakness in a system that can be exploited by malicious actors to compromise its security. These vulnerabilities can exist in various components of a software application, including its dependencies such as NuGet packages.
Given the widespread use of open-source libraries and third-party packages, modern applications often rely on a multitude of external components. While these packages can expedite development and add functionality, they also introduce potential security risks. Vulnerabilities within these packages can serve as entry points for attackers, leading to data breaches, system compromise, and other security incidents.
By integrating vulnerability checks into your DevOps pipeline, you can proactively identify and mitigate these risks early in the development process. This not only helps in safeguarding your application and sensitive data but also instills trust among users and stakeholders.
Checking Vulnerabilities in Visual Studio
For developers working with .NET projects in Visual Studio, conducting NuGet vulnerability checks is a straightforward process. Visual Studio provides built-in support for package management, including the ability to inspect package dependencies for security vulnerabilities.
Within Visual Studio, developers can utilize the NuGet Package Manager to view package details, including any reported vulnerabilities. By regularly reviewing package dependencies and staying informed about security advisories, developers can take preemptive actions to address potential risks.
Here is a screenshot of how Visual Studio displays vulnerable packages:
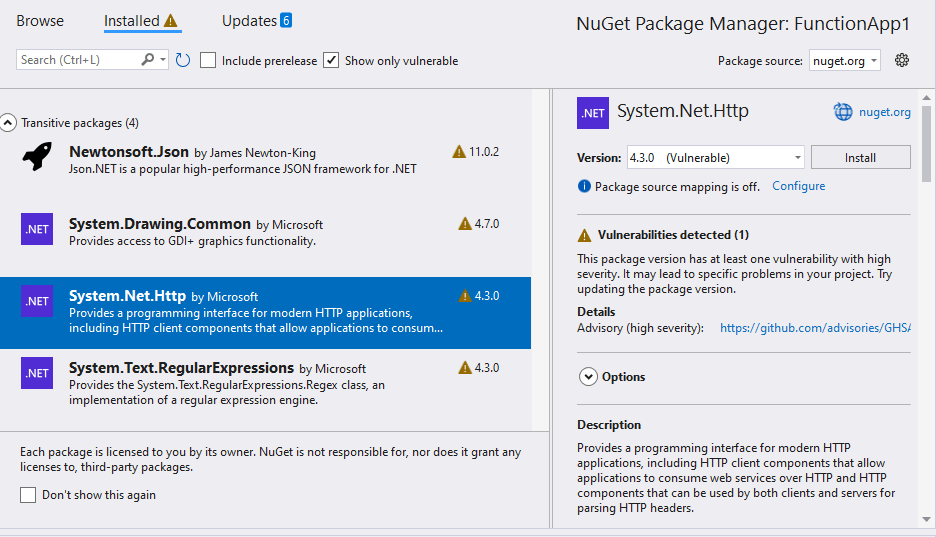 You have a checkbox for Show only vulnerable
You have a description of the vulnerability as soon you select a package.
You have a checkbox for Show only vulnerable
You have a description of the vulnerability as soon you select a package.
Adding it to the Build Pipeline
While checking for vulnerabilities within Visual Studio is crucial during development, it's equally important to incorporate this step into your build pipeline for continuous integration and deployment (CI/CD). By automating vulnerability checks as part of your CI/CD process, you can ensure that every code change undergoes rigorous security scrutiny before being deployed to production environments.
Integrating NuGet vulnerability checks into your build pipeline can be achieved using a combination of tools and plugins. Popular CI/CD platforms like Azure DevOps, Jenkins, and GitHub Actions offer plugins and integrations that enable seamless scanning of NuGet packages for security vulnerabilities.
By adding vulnerability checks to your build pipeline, you establish a proactive approach to security that aligns with modern DevOps practices. This ensures that your applications are not only functional and performant but also resilient against potential security threats.
In conclusion, securing your DevOps pipeline involves more than just writing code and deploying applications. It requires a holistic approach that prioritizes security at every stage of the development lifecycle. By incorporating NuGet vulnerability checks into your workflow, you can fortify your applications against potential threats and uphold the integrity of your software products. Remember, in the realm of cybersecurity, prevention is always better than cure.
Implementing NuGet Vulnerability Checks in Azure DevOps
- script: | dotnet tool install --global dotnet-outdated dotnet tool install --global NuGet dotnet restore dotnet list package --vulnerable --include-transitive 2>&1 | tee vuln.log echo "Analyze dotnet list package..." ! grep -q -i "has the following vulnerable packages" vuln.log displayName: 'Check for Vulnerabilities' workingDirectory: '$(Build.SourcesDirectory)'Stay secure, stay vigilant!